Architecture
The main objective of project ICOS is to design, develop and validate a meta operating system for a continuum, by addressing the challenges of:
- devices volatility and heterogeneity, continuum infrastructure virtualization and diverse network connectivity;
- optimized and scalable service execution and performance, as well as resources consumptions, including power consumption;
- guaranteed trust, security and privacy, and;
- reduction of integration costs and effective mitigation of cloud provider lock-in effects, - in a datadriven system built upon the principles of openness, adaptability, data sharing and a future edge market scenario for services and data.
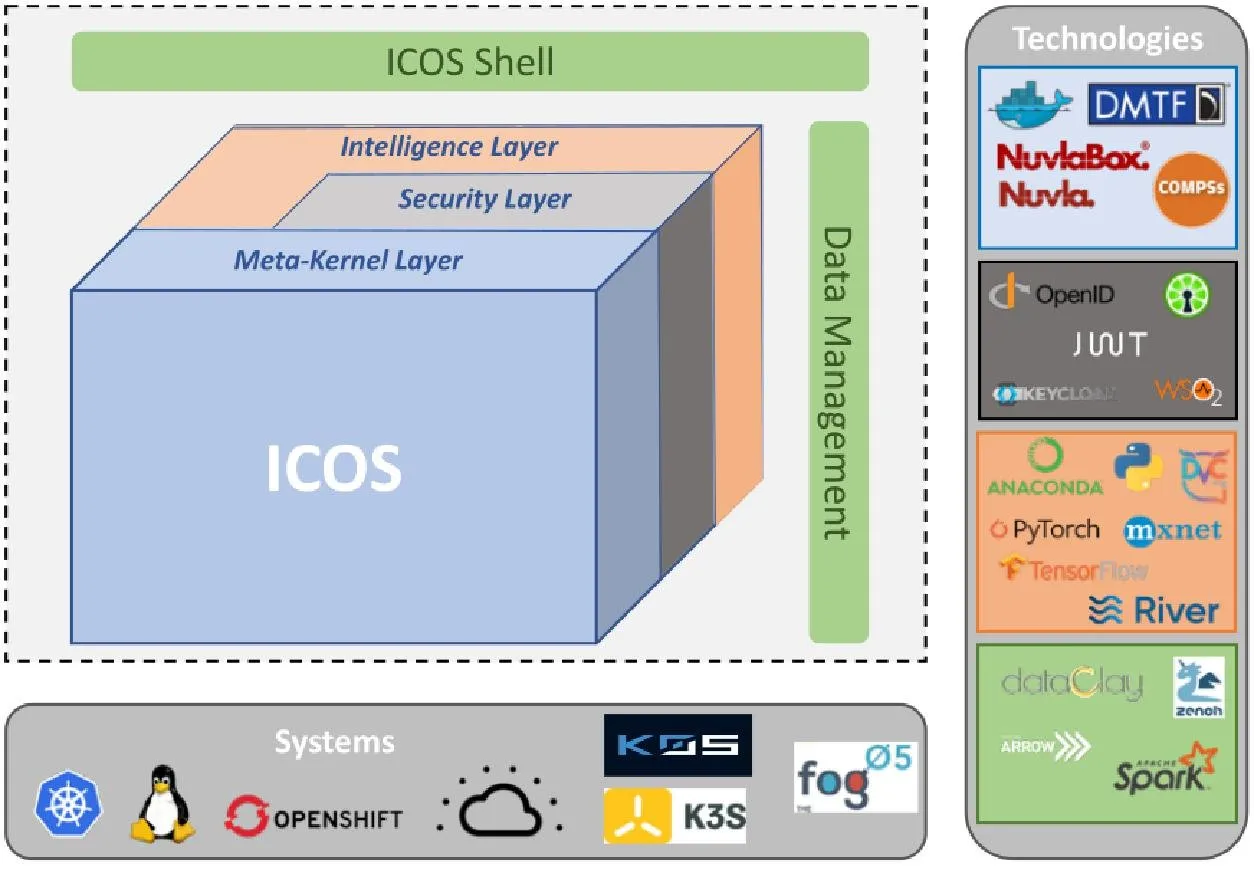
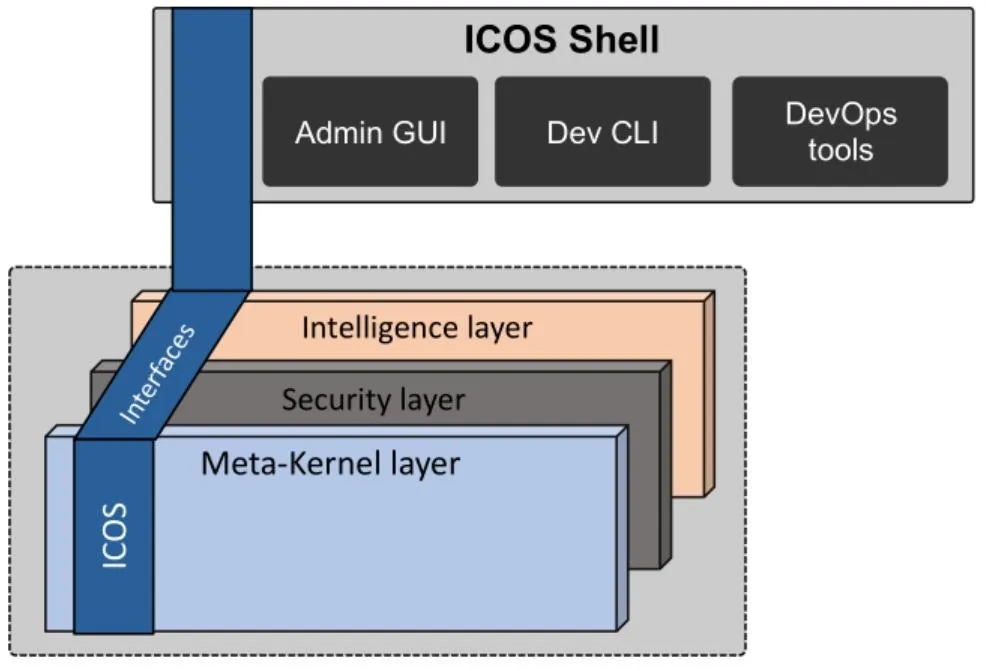
ICOS architecture consists of three main layers, Meta-Kernel, Security and Intelligence layers, as well as two additional modules, ICOS Shell and Data Management. The Meta-Kernel Layer is responsible for providing the principal OS functionalities to the continuum. It closely integrates with the Security Layer taking responsibility for guaranteeing security and trust provisioning, as well as with the Intelligence Layer that will enrich any action to be taken with innovative AI approaches. Moreover, ICOS also includes a Shell to interface users as well as a Data Management to handle all data related issues. As well illustrated in the figure is a list of candidate technologies, from today’s perspective, ICOs will use for its development.
ICOS Shell
ICOS Shell exposes the ICOS services, by means of a graphical user interface (GUI) or a command-line interface (CLI), and it also provides a set of Development and Operations (DevOps) tools to facilitate the development lifecycle. Thus, ICOS shell provides an interface between the system administrator or the developer, and the proposed ICOS intelligence, security and meta-kernel layers. The ICOS shell module consists of three main components:
- The Administrative Graphical User Interface (Admin GUI): is an environment that will be used by systems administrators responsible for deployment and runtime management of apps, services and tasks provided by ICOS. The Admin GUI may be used to introspect and control the state of the apps, services and tasks, running in the intelligence, security and meta-kernel layers.
- The Developers Command Line Interface (Dev CLI): is an environment that will provide interactive access to ICOS systems functions or services that are not available in the graphical interface.
- The DevOps tools: is a set of tools to facilitate coding, building, testing, packaging, releasing, configuring and monitoring of applications in the ICOS system as well as to provide automation tools for developers and system administrators.
Data Management
The Data Management Module is responsible for managing all data required in ICOS, as well as the efficient execution layer of data-based applications and services used in ICOS. Its main functionalities include:
- Data distribution across the continuum, taking advantage of the entire available infrastructure Smart data placement and dynamic adaptation to changes in the infrastructure during operation: devices joining or leaving, reorganizations, etc
- Seamless access to data in ICOS, regardless of the location (device or cloud) or nature of resource (in-motion or at-rest), by providing an integrated data platform spanning the whole continuum
- Minimization of data transfers to improve performance and trust, by exploiting near-data processing invarious types of devices.
Intelligence Layer
This layer provides functionality to train, test, use, maintain and update analytics and machine learning models in the continuum, with the goal of supporting and augmenting the operations and performance of the security and meta-kernel layers by considering specific policies in the use of data and models, with special emphasis in trustworthiness (see Fig. 1.6), including:
- Intelligence Layer Coordination: Coordination enables optimization and predictive analytics and machine learning models and its use across the continuum. This will include policies for the use, share and update of models across the edge-cloud continuum, including federated learning strategies. Data Processing: Data processing and storage in formats and databases optimized for the application of analytics tasks depending on the resources available of the hosting device in the continuum.
- AI Analytics: A library of optimized machine learning algorithms for the training and testing of predictive and optimization models, including deep learning, adaptive machine learning and reinforcement learning libraries optimized to operate in constrained devices. The ICOS Gitlab repository to manage all algorithms and libraries employed in the different version of the meta-OS will be maintained, such that, depending on the constraint of the device, only the required functionality will be fetched at installation or update time.
- AI Models Marketplace: A collection of pre-trained analytics and ML models to be reused, updated, refined (e.g., transfer learning) and combined to foster the application of new AI techniques in the different layers of the ICOS meta-OS. Functionality to train and compress these models for operation in constrained devices will be provided (e.g., pruning unused branches in trees or simplifying Neural Network architectures). The models will be stored in the so-called ICOS AI Models Marketplace.
- Trustworthy AI: Provide specific algorithms to analyze the datasets and develop models conforming to policies for privacy and trustworthiness. Functionality for models to be trained in a federated learning fashion to ensure data protection in datasets containing user-specific data will be provided as well as explainable AI algorithms to provide reassurance of output of models to the different layers in ICOS. Security Layer
This layer includes:
- Federated Identity Management;
- Authentication, Authorization and Audit capabilities;
- Detection of security issues and mitigation mechanisms (e.g. self-healing);
- Support for compliance frameworks, and;
- Trust and privacy, as supported by several architectural components:
Federated Identity Management and Access Control – AuthT and AuthZ libraries will be made available for usage by third-parties.
Audit Module will provide audit capabilities based on different standards, such as OpenID Connect, which will allow insight into data and compute flow throughout the continuum.
Security Assessment will be used to detect potential security issues and already recommend specific mitigation or recovery processes.
Recovery Module will provide a catalogue of recovery processes that may be atomatically enforced.
Anomaly Detection Mechanisms will be built on top of the Intelligence layer and will provide input to the Recovery and Security Assessment module.
Privacy Module will provide a set of primitives that could be used for data transformation, such as anonymisation, and encryption.
Trust Module will provide the framework for attesting that the environment has not been tampered.
Compliance Enforcement Module will enable detection of compliance problems and enforce infrastructural changes in order to enhance compliance based on the chosen target compliance framework.
Distributed Meta-Kernel Layer
The Meta-Kernel Module provides the base functionalities necessary to make edge devices manageable and ICOS-ready. It is built on the following set of well defined components (see figure below):
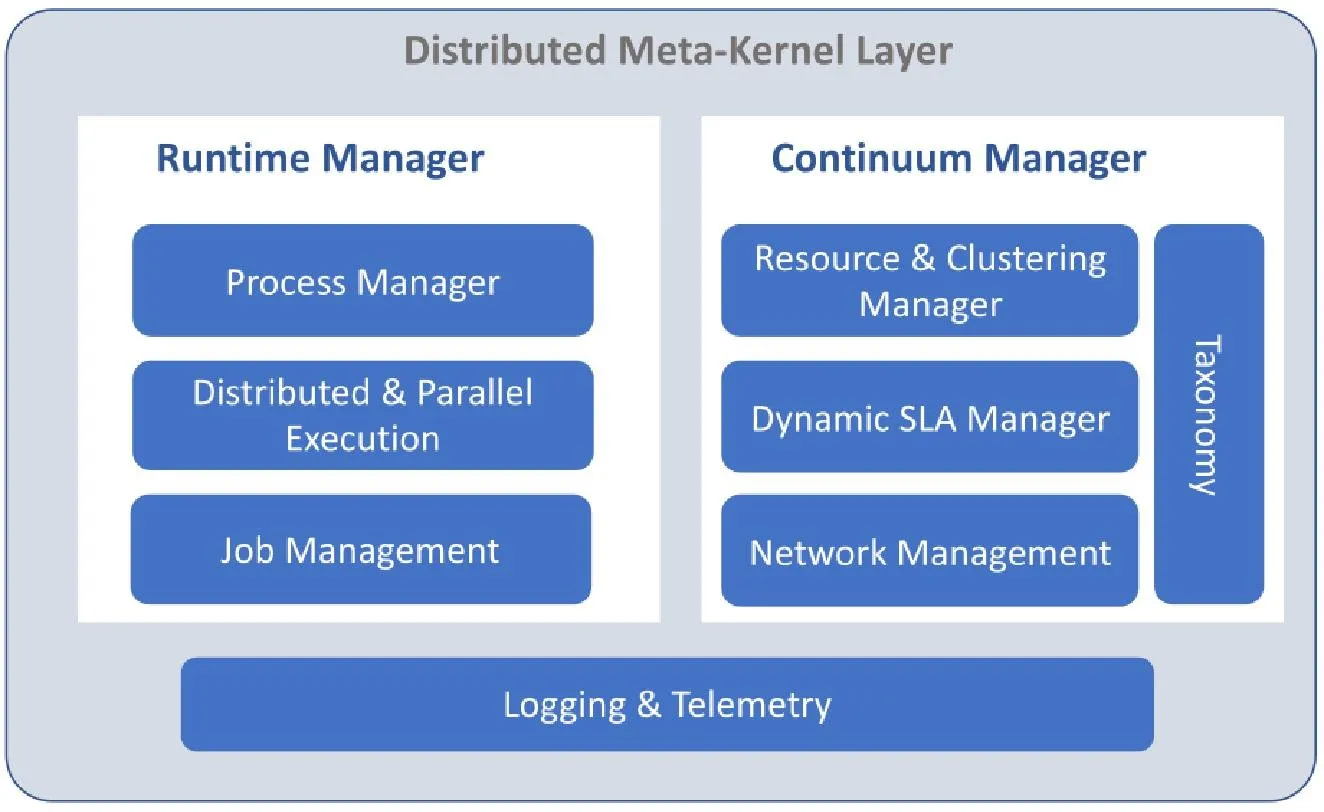
Runtime Manager: responsible for ensuring the underlying devices to fulfill service requirements deployed from the upper layers of the ICOS ecosystem (i.e., the ICOS Shell) to provide a high-performance execution. For that purpose, the runtime manager will:
- convert the workload of the invocation into a workflow of tasks (including native methods, binaries, containers, FaaS operations deployed beyond the ICOS ecosystem, etc.) and orchestrate their execution by distributing them across the computing devices within the continuum;
- facilitate the deployment of optimized ICOS components partitioning, resource allocation and placement functions, towards a green strategy enforcing policies like energy efficiency with special attention to green energy or carbon usage effectiveness, location, infrastructure associated costs, etc..
In order to adapt to the rapidly changing infrastructure, the task scheduling system of the runtime manager will be provided with malleability and fault-tolerance mechanisms to quickly react to the changes.
Continuum Manager: responsible for bootstrapping new devices into the ICOS continuum. It provides the mechanisms for:
- registering and activating the edge devices into ICOS Shell;
- enabling the remote execution of management jobs, issued by users, allowing for on-demand management and re-configuration of the Meta-Kernel itself, as well as low-level operations such as real time configuration, kernel tunning or updates/upgrades (including mechanisms to automatically enforce green strategies such as: offloading of computation-intensive tasks –from end users to edge nodes or the cloud–, configuring edge-device CPU processor, connectivity and bandwidth utilization, resources location, etc.);
- configuring the edge device’s network such that secure remote access, multi-access edge computing and network attack surface protection can be enabled;
- ensuring that the user workloads and the underlying device are performing according to the expectations mandated by pre-defined and configurable SLA criteria. The component also makes sure that failed workloads are rebalanced and quality is reinforced, and;
- discovering, labeling and categorizing both the underlying device and all relevant peripherals such as IoT sensors and actuators.
Logging and Telemetry: responsible for collecting and uploading telemetry reports into ICOS Shell. Such logs shall be accessible both locally from within the edge device and remotely from the ICOS Shell. This component will also support the exchange of metrics and information between the Meta-kernel and user workloads.
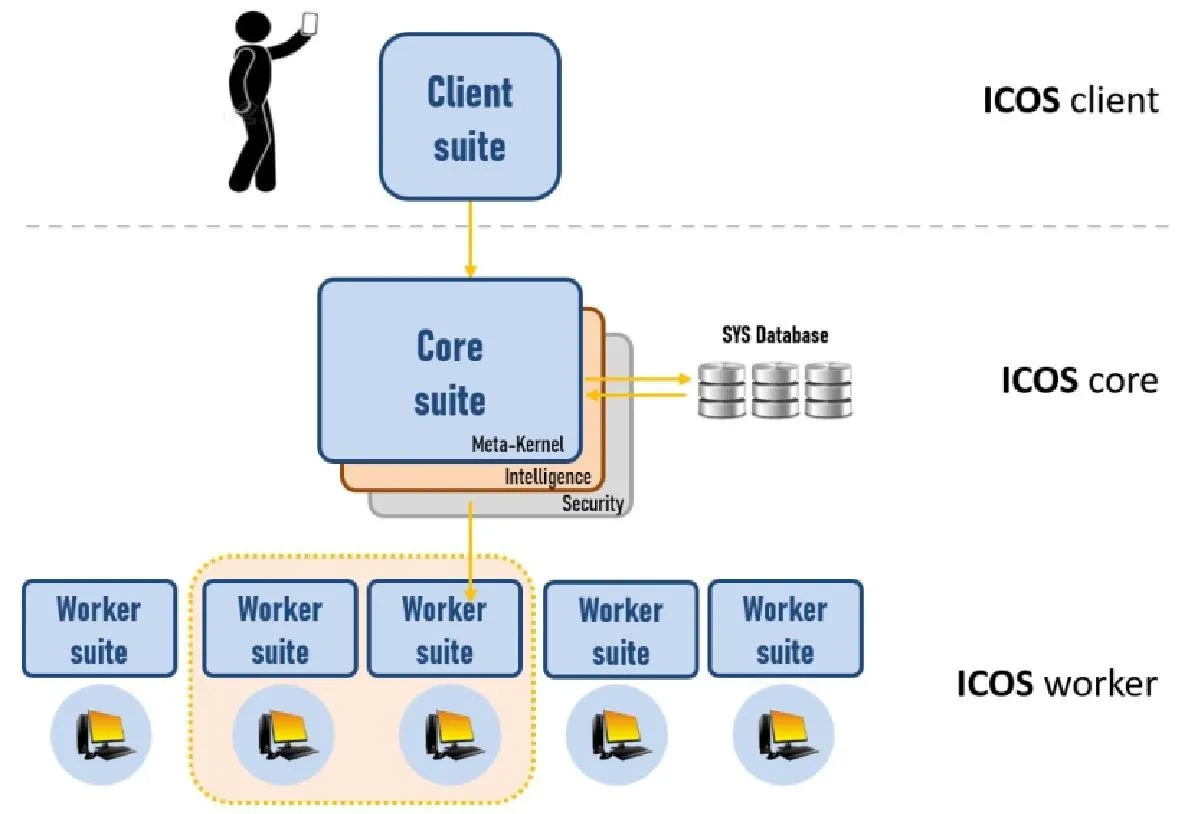
ICOS Platform delivery suites
Three different functional roles are envisioned in the ICOS system: system client, system core, and system workers. For this reason, three delivery suites are provided accordingly.
The system client may be either a user with a device or a device programmed to launch commands to the system. In either case, the Client suite contains the user's shell with basic operational commands (service launching, users' configuration, etc.), monitoring capabilities and, optionally, the development tools kit and an interactive GUI.
The system core is the responsible for all system control and management tasks defined in the ICOS architecture, and includes Meta-Kernel layer, Security layer, and Intelligence layer. Consequently, the Core suite implements all these functionalities and is, by far, the most complex system component.
The system workers shape the set of available running devices in ICOS to effectively execute all system service executions. The Worker suite is a lightweight component with the basic run-time libraries to enable the execution of off-loaded tasks and subtasks. Delivery suites will be installed in devices according to the device's role in the system, i.e., whether a client (Client suite), part of the system core (Core suite) or one of the multiple system workers (Worker suite). Each suite can be delivered as a complete package or delivered selectively as isolated components as part of the ICOS solution, to facilitate reuse and updating. Furthermore, note that a physical device can install more than one suite instance if desired, assuming several roles in the system. For instance, one can install a Client suite and a few Worker instances in a smartphone, a Core suite and several Worker instances in one server, or just a Worker instance in a low-power device.